Next Generation Privacy: Navigating the Privacy Continuum with End-to-End Privacy Risk Management
Introduction
Technology has changed the way organizations conduct business. Millions of transactions with personal information are transmitted as data packets across jurisdictions and boundaries. Organizations must not only protect the personal data of their customers, but their employees as well. They are responsible for the data in their possession and must ensure that the privacy of these individuals is protected. This requires a constant process of monitoring their systems for weaknesses and implementing privacy and security practices that evolve as conditions change. Organizations are responsible for managing voluminous buckets of data while implementing an efficient way to manage their operations. They must also deal with an evolving attitude and outlook of the next generation of customers and employees that rely heavily on technology and have no qualms about providing their personal data to conduct personal business online.
Background
Data privacy focuses on protecting an individual’s information and giving them the choice to decide how their information should be used. Data is continuously created, manipulated, and flows through interconnected systems or continuum. In order to flow effectively, organizations must manage the different stages of data that are all dependent on each other. From data creation, manipulation, use, storage and eventually data destruction, there is an inherent responsibility of protecting the data through the whole data continuum life cycle. There are numerous implications and problems that could arise at any point. When one stage is affected, it will ultimately have a domino effect on the rest of the life cycle. Recent events have shown that the concern in protecting the data is elevated when it includes personal information. The sources of the personal information could be external customers, internal employees, or other business partners/organizations. Once personal data enters an organization’s system, they are responsible for ensuring that it is protected while in their possession.
Recent privacy breaches have revealed that organizations are susceptible to intrusions and their customers’ and employees’ information are at risk of being compromised. Changes and passage of various laws and regulations in the European Union, United States Federal agencies, and state governments indicate that regulators are aware that there is a growing trend and that organizations need to be held more accountable in protecting the privacy of individuals. Organizations, such as financial entities, healthcare providers, and governmental agencies, are all required to have privacy controls that would protect individual’s privacy and personal information. The reality is that many organizations are lacking in this area and there is a growing need to implement an effective privacy program that not only protects their company’s assets, but protect personal information as well.
Personal data is extremely valuable because it allows an organization to target customers, advertisers to reach a wider audience, or even drug companies to recommend a specific drug or medical treatment. It also allows an organization to effectively manage its human capital and employees. As information flows through an organization, each function represents a data point that requires some level of protection or controls. A privacy disruption or breach on one bucket of data could expose vulnerabilities in an organization’s overall infrastructure. For example, in an Energy Utility company, there are different components that have and use personal data for different functions within the company. Human Resources manages the personal data of employees, applicants, and contractors. Billing, Customer Service, and Account Services have the personal data of customers. Technology and Customer Outreach manage the mobile apps and outreach to potential or current customers. All of these buckets of personal data feed into the overall structure of the company. If the data is exposed or one of the points is compromised interrupted or breached, the rest of the process is affected. The consequences of a privacy breach could have negative impacts on an organization ranging from interrupted services and operations, monetary fines and losses, decline in customer confidence, and loss of revenue. The damage and impact is distinguishable from a cybersecurity incident because personal data impacts individuals differently and it is difficult to place a value on the damage that will be or may have been caused by the breach.
It is critical to ensure that all these entities share the responsibility of implementing privacy practices and controls that will protect personal data. Rather than just focusing on their individual functions, organizations need to implement an overarching privacy blueprint at the enterprise level that minimizes privacy risk and impact. The privacy world is a convoluted process and most organizations lack the resources to determine where and when privacy should be implemented, who should be involved in the process, and who ultimately assumes the overall responsibility for implementing privacy. Organizations are now more heavily regulated for possessing personal information. Individuals have more opportunities to take control and determine how their information is used and who has access to their personal information.
Organizations must also deal with the next generation of customers and employees. This generation relies heavily on technology and most likely assumes that their information is safe with the organization and has taken the necessary steps to secure the information. The changing workforce and customers are much more willing to provide personal information with less skepticism and a higher level of trust. Organizations must implement privacy practices that address the issue that they possess more personal information and the level of data protection and security required is relative to the amount of data that an organization possesses. In other words: more data, more protection. How does an organization successfully navigate the data privacy continuum, while ensuring that they are providing the highest quality service to their customers and employees? Organizations must be able to implement privacy practices that compliment and address privacy in today’s context for the next generation.
Figure 1 – Evolution to PRM
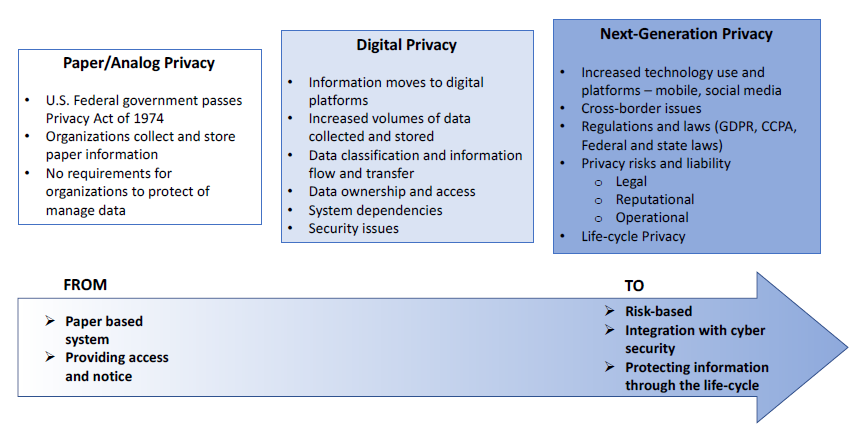
Navigating the Data Privacy Continuum: Rising Sun’s Privacy Risk Management (PRM) Approach
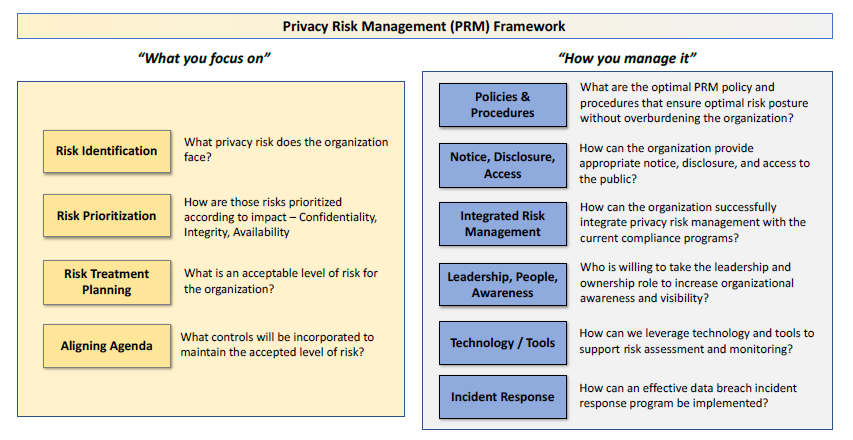
Executing Rising Sun’s PRM approach within an organization begins with the identification of the greatest information privacy risks across the organization. The goal of this approach is to implement a privacy by design approach from the top down and to integrate with an organization’s information security and privacy strategy for mitigating these risks. This approach designs a data privacy mapping plan that assesses the type of personal data collected, creates an inventory, and determines where the potential impacts and privacy risks throughout your organization lie. The resulting PRM framework provides a continuous process to adjust readily to new information privacy risks and opportunities, based on the strategic priorities and the operational tempo of the department – all aligned under a policy. The approach will ensure that all individuals in your organization are given the knowledge and understanding they need to protect data and think privacy first. The PRM framework enables management to make educated trade-off decisions, balancing costs and benefits of pursuing a specific information privacy risk posture. There are six essential components of Rising Sun’s PRM framework:
Policy and Procedures. The policy and procedures should identify the specific organizational roles and responsibilities that support all PRM activities, as well as capture the accepted information privacy risk posture for the organization. These documents should be developed in coordination with system owners and other stakeholders to ensure that the PRM approach accomplishes the mission and goals of the organization.
Notice, Disclosure, and Access. The organization should develop a process that ensures compliance with applicable laws and other regulatory requirements. This ensures that the organizations functions are transparent when it collects, controls records, and stores personal information. Organizations should not disclose, share, or sell information about individuals from without the written consent of the individual. The organization must also allow individuals access to their information and be able to decide how that information is used. Integrated Risk Management. Organizations should develop and integrate privacy risk management processes with information security and manage the activities of risk identification, prioritization, risk treatment planning, and the implementation of specific privacy risk controls. Each process should also support the adherence to the appropriate regulations and guidance (e.g., U.S. Privacy Act, General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA)).
Leadership, People and Awareness. The PRM framework should be forged not only by those who are routinely responsible for risk management and security responsibilities, but protecting individuals should be everyone’s concern. The organization should provide the proper privacy training to ensure that awareness throughout the department is increased.
Technology/Tools. The organizations will leverage analytical tools and technology to improve privacy risk decision making and responses to information risk as it changes; measure risk mitigation with clearly defined benchmarks; monitor the organization’s risk profile; and implement best-practice information risk mitigation solutions.
Incident Response. Ensure that an effective program to Detect, Respond and Recover when a privacy and/or security incident occurs. Informing the internal stakeholders and public that there is a structured incident response program will increase awareness and encourage reporting.
Components of Rising Sun PRM Framework
Summary
Rising Sun’s Privacy Risk Management approach is designed to work collaboratively with organizations in navigating the data privacy continuum. Our framework reviews an organization’s functions and operations to determine where privacy can be successfully implemented as tailored to the specific environment – there is no “one-size-fits-all” model for Privacy. The PRM will continuously monitor the effectiveness of the program, while ensuring that an organization accomplishes its mission and operates without interruption or delay.
What Rising Sun Advisors Brings
Rising Sun Advisors has significant experience and unique expertise in implementing PRM solutions. Our consultants have successfully implemented the PRM framework at government and non-government organizations. By adopting Rising Sun’s PRM framework and focusing on specific risk drivers, these organizations have been able to effectively streamline and focus privacy risk operations and enhance compliance to prescribed laws and regulations – driving improved results on score cards (e.g., FISMA), improving awareness of privacy risks for “non-technologists”, and improving the overall risk posture for the organization. Some specific examples that showcase our thought leadership in implementing PRM in the other government agencies are outlined below:
- We assessed the privacy risks for multiple IT programs and systems at a Federal agency.
- We enabled a Federal agency to develop its Risk Management Framework by integrating Privacy and Security controls in the system authorization process.
- We conducted Privacy training sessions to educate system owners and other security and privacy personnel about the integrated Privacy and Security process.
- We drafted and revised acquisition and contract guidelines to include cyber security and privacy requirements.
Our work with these government agencies provides dramatic evidence that implementing PRM is a necessary requirement in today’s digital environment – which is only exponentially increasing. Although not all risks can be anticipated, they can be managed – by senior executives, boards, and stakeholders working together to accept and maintain the appropriate level of information risk. With stakeholder expectations higher than ever, more and more organizations (private and public) have begun to implement PRM to secure considerable benefits.
Leadership Bios
 Mr. Miheer Khona is the President & CEO of Rising Sun Advisors with over 15 years of experience in Strategy, Transformation and Governance at the intersection of Cyber Security and Information Risk Management. Mr. Khona brings with him a strong analytical and engineering background in serving the needs of various clients in private and public sectors, including U.S. and International Governments. He led the efforts in developing the Financial Services domain of Internet Security Alliance’s Cybersecurity Social Contract publication – blending the realms of politics, economics, and cyber security viewpoints into a market-based implementation model for the current U.S. Executive Office of the President (EOP) and the Congress. Prior to founding the boutique management consulting firm, he successfully led the design and execution of a next-generation Global Operating Model for a Bank of New York Mellon’s Information Risk Management Division as the Head of Information Risk Strategy & Transformation. Prior to a career in financial services, Mr. Khona provided strategic and technical analysis of global information security programs and developed enterprise risk management frameworks for multiple clients in the commercial and public (U.S. and international governments) sectors as a management consultant. A sampling of clients that Mr. Khona has had the privilege of serving includes, International Governments, U.S. Department of Energy, U.S. Department of Transportation, U.S. Department of Commerce, a Global Retail & Investment Bank, World Bank Group, Depository Trust and Clearing Corporation (DTCC), Fannie Mae, Global Commercial & Retail Bank.
Mr. Miheer Khona is the President & CEO of Rising Sun Advisors with over 15 years of experience in Strategy, Transformation and Governance at the intersection of Cyber Security and Information Risk Management. Mr. Khona brings with him a strong analytical and engineering background in serving the needs of various clients in private and public sectors, including U.S. and International Governments. He led the efforts in developing the Financial Services domain of Internet Security Alliance’s Cybersecurity Social Contract publication – blending the realms of politics, economics, and cyber security viewpoints into a market-based implementation model for the current U.S. Executive Office of the President (EOP) and the Congress. Prior to founding the boutique management consulting firm, he successfully led the design and execution of a next-generation Global Operating Model for a Bank of New York Mellon’s Information Risk Management Division as the Head of Information Risk Strategy & Transformation. Prior to a career in financial services, Mr. Khona provided strategic and technical analysis of global information security programs and developed enterprise risk management frameworks for multiple clients in the commercial and public (U.S. and international governments) sectors as a management consultant. A sampling of clients that Mr. Khona has had the privilege of serving includes, International Governments, U.S. Department of Energy, U.S. Department of Transportation, U.S. Department of Commerce, a Global Retail & Investment Bank, World Bank Group, Depository Trust and Clearing Corporation (DTCC), Fannie Mae, Global Commercial & Retail Bank.
Mr. Khona currently serves on the Economic Development Subcommittee for the Governor of Maryland’s Cyber Security Council, and is a Board Member of the School of Applied Sciences & Technology at Thomas Edison State University. Mr. Khona holds Bachelor of Science degree in Information Technology from the Volgenau School of Engineering at George Mason University, and an Executive Master of Business Administration (MBA) degree from Brown University and Instituto de Empresa (IE Business School). Mr. Khona has also held the following designations: Certified Information Systems Security Professional (CISSP), Security+, ISO/IEC 27001 ISMS Lead Auditor, ISO/IEC 27001 Information Security Risk & Implementation Practitioner.



